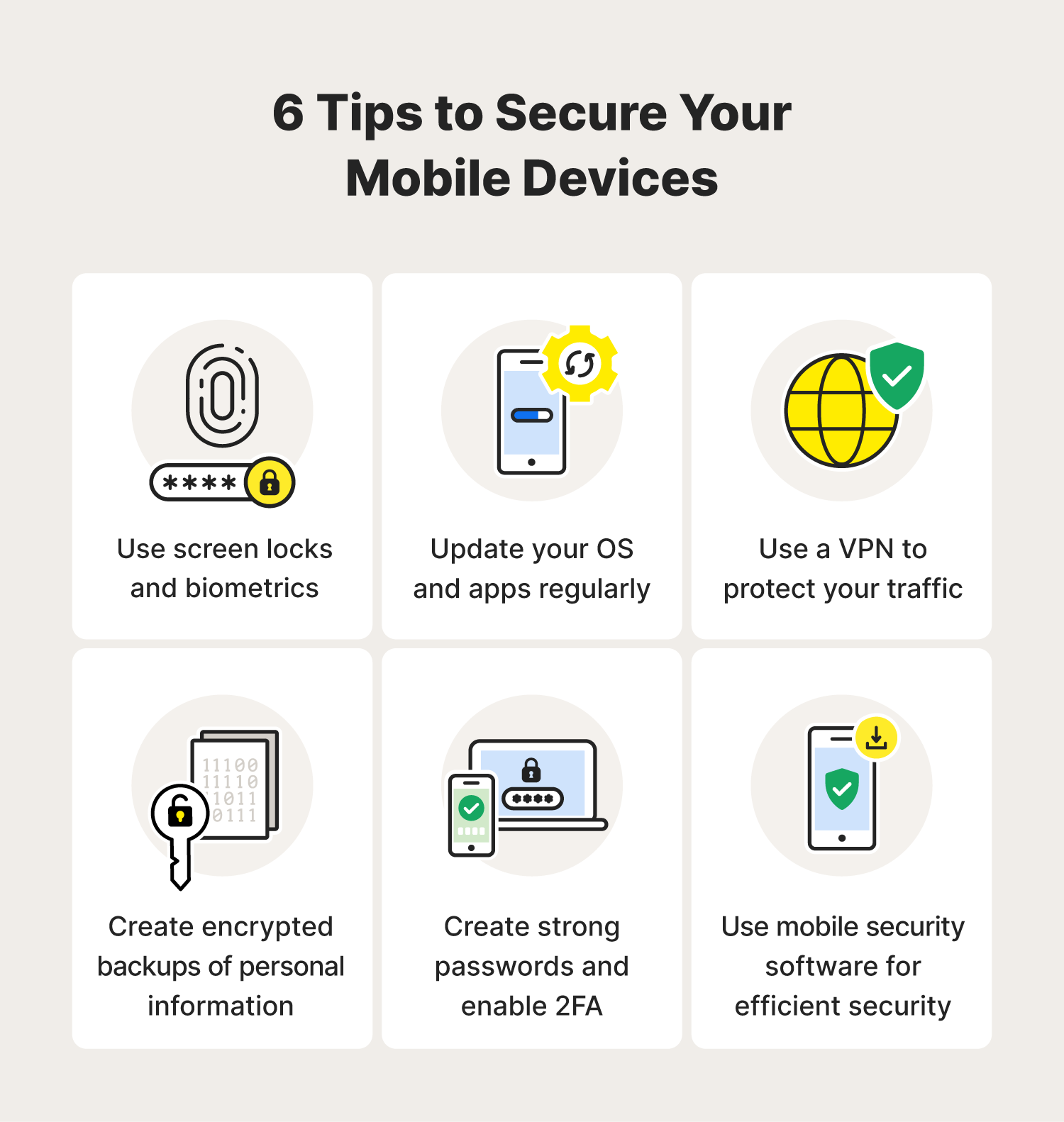
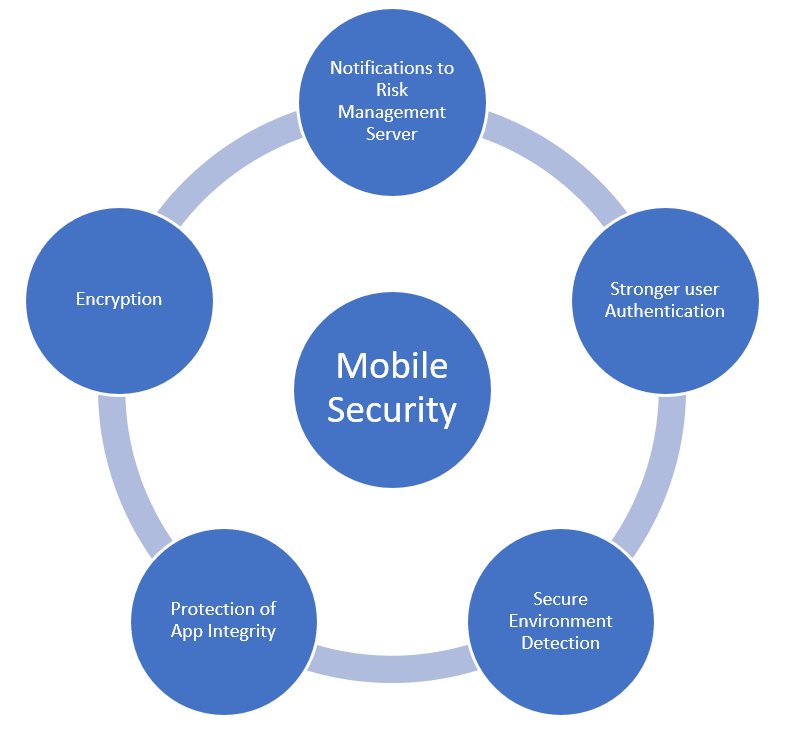
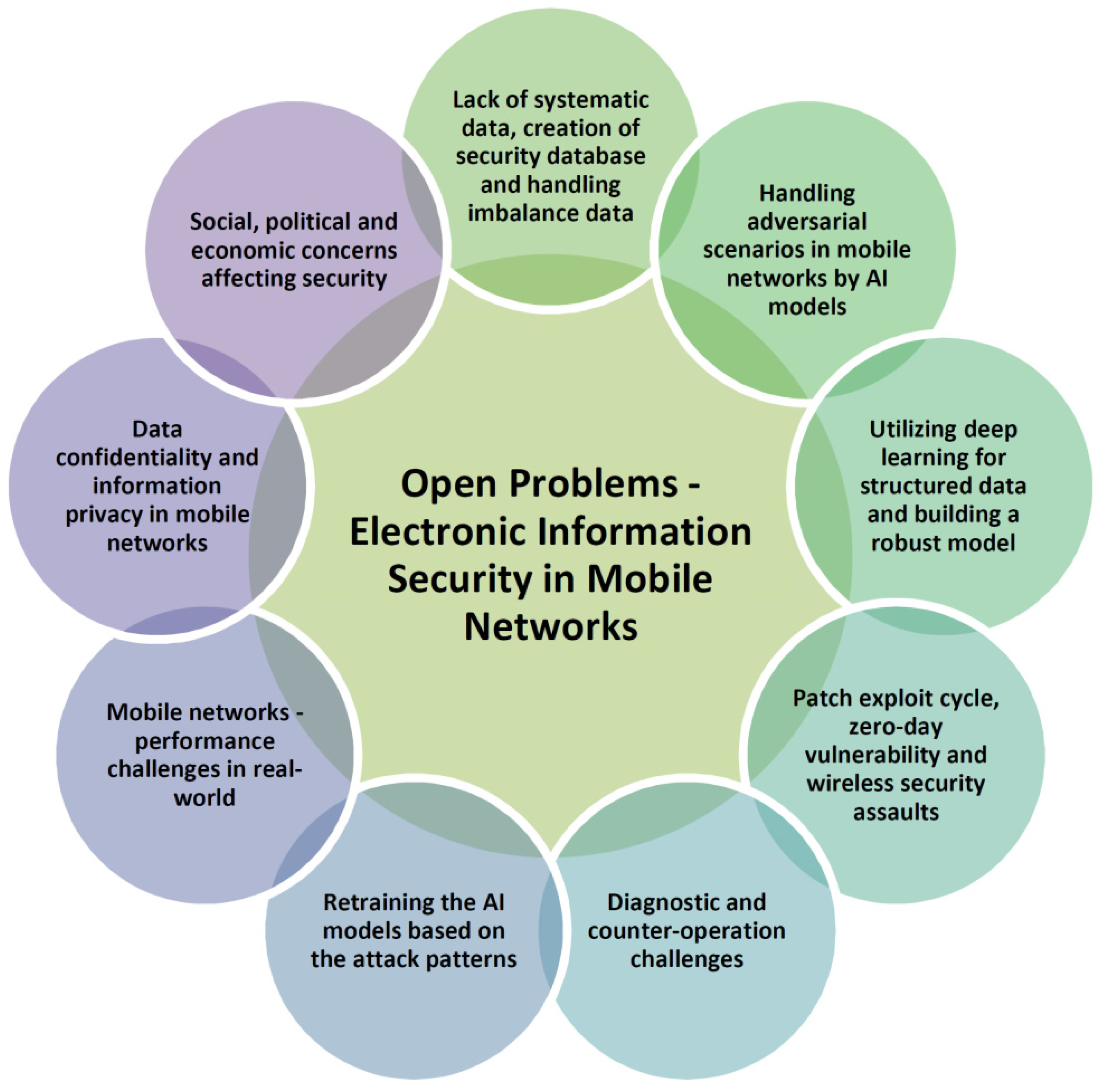
Future research directions-electronic information security in mobile... | Download Scientific Diagram
![Architecture of Mobile database security [1] From Fig. 1, it can be... | Download Scientific Diagram Architecture of Mobile database security [1] From Fig. 1, it can be... | Download Scientific Diagram](https://www.researchgate.net/publication/322465819/figure/fig1/AS:582255156142080@1515831855515/Architecture-of-Mobile-database-security-1-From-Fig-1-it-can-be-seen-that-security-is.png)
Architecture of Mobile database security [1] From Fig. 1, it can be... | Download Scientific Diagram
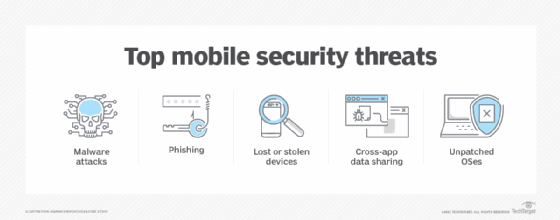
Sensors | Free Full-Text | A Systematic Review on Machine Learning and Deep Learning Models for Electronic Information Security in Mobile Networks

Smartphone and the security of your data #INFOGRAPHIC | Mobile data, Mobile security, Online security